rfid write protection This publication seeks to assist organizations in understanding the risks of RFID technology and security measures to mitigate those risks. It provides practical, real-world advice on how to initiate, design, implement and operate RFID systems in a manner that mitigates security and privacy risks.
Oct 19, 2018. #1. Hi, I need to develop an APP to read a NFC card in backgroung and to paste the code to the active application. The behavior should be like the barcode reader. For example, I .Mi Note 2. Android. Xiaomi. Mi Note 3. Android. Here is the list of all the smartphones and tablets with the feature of NFC. NFCTagify list of NFC supported gadgets make it easy for the users to choose the best device for .
0 · what is rfid technology
1 · what is rfid security
2 · what is rfid card
3 · rfid em4305
4 · rfid data storage
5 · rfid bar code meaning
6 · are rfid tags safe
You will need an amiibo figure or card, a compatible game, and a Nintendo Switch, Nintendo Switch Lite, or New Nintendo 3DS XL system. For use with Nintendo 3DS, Nintendo 3DS XL and Nintendo 2DS systems, a Nintendo 3DS .
The purpose of this document is to outline a common process for write-protecting the EPC memory bank of UHF RFID tags while avoiding technical details that may become antiquated or vary between RFID chip supplier.
The purpose of this document is to outline a common process for write-protecting the EPC memory bank of UHF RFID tags while avoiding technical details that may become antiquated or vary between RFID chip supplier.
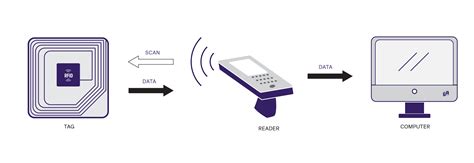
Learn how to store data securely on RFID cards with this comprehensive step-by-step guide. Discover RFID card types, data storage methods, and best practices for ensuring data security and operational efficiency. RFID stands for radio-frequency identification. A small chip -- known as an RFID tag -- is attached to or implanted in an object. The tags contain information that can be read at short range via radio waves. The chip and reader don't have to touch. Some RFID tags can be powered by a battery, but many RFID tags aren't self-powered. We believe the best way to avoid tear-off against Protection Words on EM4305 is to enable the password for WRITE/PROTECT commands. This can be done by setting the Write Login bit co20 in the configuration word (word 4). This publication seeks to assist organizations in understanding the risks of RFID technology and security measures to mitigate those risks. It provides practical, real-world advice on how to initiate, design, implement and operate RFID systems in a manner that mitigates security and privacy risks.
what is rfid technology
Can an RFID blocking card keep someone from "reading" your card without your knowledge? I put it to the test. Credit and debit cards contain RFID contactless technology.
One of the easiest ways to prevent RFID hacking is to invest in badges and wallets that block RFID signals. RFID blockers prevent both scanners and legitimate readers from scanning your card so using it off-premises is the perfect way .To protect your RIFD database, make sure you mitigate database related vulnerabilities and risks. Despite being a target of some common attacks, RFID is gaining popularity in certain areas because of its low-maintenance cost and cost-effectiveness.
The best way to protect yourself from RFID-related identity theft is by investing in RFID-blocking products like wallets, backpacks, fanny packs, and even pant pockets. RFID blocking is the process of making your RFID-enabled device resistant to unauthorized access. The most popular way to achieve this is by getting an RFID blocking wallet — a holder for your cards that is made from materials that interfere with electromagnetic fields.
what is rfid security
The purpose of this document is to outline a common process for write-protecting the EPC memory bank of UHF RFID tags while avoiding technical details that may become antiquated or vary between RFID chip supplier.
Learn how to store data securely on RFID cards with this comprehensive step-by-step guide. Discover RFID card types, data storage methods, and best practices for ensuring data security and operational efficiency. RFID stands for radio-frequency identification. A small chip -- known as an RFID tag -- is attached to or implanted in an object. The tags contain information that can be read at short range via radio waves. The chip and reader don't have to touch. Some RFID tags can be powered by a battery, but many RFID tags aren't self-powered. We believe the best way to avoid tear-off against Protection Words on EM4305 is to enable the password for WRITE/PROTECT commands. This can be done by setting the Write Login bit co20 in the configuration word (word 4). This publication seeks to assist organizations in understanding the risks of RFID technology and security measures to mitigate those risks. It provides practical, real-world advice on how to initiate, design, implement and operate RFID systems in a manner that mitigates security and privacy risks.
what is rfid card
Can an RFID blocking card keep someone from "reading" your card without your knowledge? I put it to the test. Credit and debit cards contain RFID contactless technology. One of the easiest ways to prevent RFID hacking is to invest in badges and wallets that block RFID signals. RFID blockers prevent both scanners and legitimate readers from scanning your card so using it off-premises is the perfect way .
To protect your RIFD database, make sure you mitigate database related vulnerabilities and risks. Despite being a target of some common attacks, RFID is gaining popularity in certain areas because of its low-maintenance cost and cost-effectiveness. The best way to protect yourself from RFID-related identity theft is by investing in RFID-blocking products like wallets, backpacks, fanny packs, and even pant pockets.
rfid em4305

rfid data storage
rfid bar code meaning
Learn how you can enable or disable NFC mode on the Google Nexus 5.FOLLOW US ON TWITTER: http://bit.ly/10Glst1LIKE US ON FACEBOOK: http://on.fb.me/ZKP4nUFOLL.
rfid write protection|what is rfid security