hacked with a micro sd card with nfc chip If your debit card has an NFC chip on it (the "tap to pay"), it's possible. This presentation discusses two methods. One is skimming an NFC . Place your Proxmark3 between the tag and the AMS. Recommended: Use tape to hold it in .Scroll down until you see the “NFC and payment” option and tap the toggle on the right side of the screen. Return to your home screen. Tap the “Home” button, which is the middle of the three buttons at the bottom of your device. Hold your phone against the NFC tag.
0 · nfc debit card scam
1 · nfc debit card clone
2 · cloning nfc card while in pocket
The Secure Element chip, an NFC chip that contains data such as the Secure Element identifier (SEID) for secure transactions. This chip is commonly found in smartphones and other NFC devices. Near-field communication (NFC) is a set .
Cybercriminals have reportedly found a way to steal from smartphone users by . If your debit card has an NFC chip on it (the "tap to pay"), it's possible. This presentation discusses two methods. One is skimming an NFC . A new Android malware named NGate can steal money from payment cards by relaying to an attacker's device the data read by the near-field communication (NFC) chip. Specifically, NGate enables. ESET security researchers have discovered a new type of Android malware, .
Cybersecurity researchers have uncovered new Android malware that can relay . Debit cards with NFC can be easily hacked to make fraudulent cash withdrawals .
The cyberattack, based on both a complex social engineering scheme and the . The new chip-enabled credit cards that banks are sending their customers are .
nfc tag wifi iphone
The flaws make them vulnerable to a range of problems, including being .
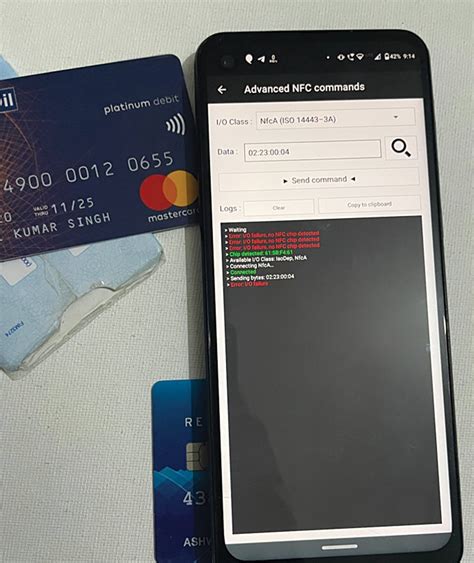
Newly discovered Android malware steals payment card data using an infected device’s NFC reader and relays it to attackers, a novel technique that effectively clones the card so it can be used. Cybercriminals have reportedly found a way to steal from smartphone users by exfiltrating the data read by their device's near-field communications (NFC) chip. If your debit card has an NFC chip on it (the "tap to pay"), it's possible. This presentation discusses two methods. One is skimming an NFC card and using the recovered data for making Card Not Present transactions online.
A new Android malware named NGate can steal money from payment cards by relaying to an attacker's device the data read by the near-field communication (NFC) chip. Specifically, NGate enables.
ESET security researchers have discovered a new type of Android malware, which they call NGate. It can interact with a device’s NFC traffic, capture it from apps that use NFC, and relay the data to a malicious actor, who can then mimic or replay the intercepted data. Cybersecurity researchers have uncovered new Android malware that can relay victims' contactless payment data from physical credit and debit cards to an attacker-controlled device with the goal of conducting fraudulent operations. Debit cards with NFC can be easily hacked to make fraudulent cash withdrawals and payments. But experts aren’t too worried about it in India. Here’s the reason for that.
The cyberattack, based on both a complex social engineering scheme and the use of a new Android malware, is capable of stealing users’ near field communication data to withdraw cash from. The new chip-enabled credit cards that banks are sending their customers are supposed to make it more difficult for thieves to steal consumers' account information when they're using their. The flaws make them vulnerable to a range of problems, including being crashed by a nearby NFC device, locked down as part of a ransomware attack, or even hacked to extract certain credit card.
Newly discovered Android malware steals payment card data using an infected device’s NFC reader and relays it to attackers, a novel technique that effectively clones the card so it can be used.
Cybercriminals have reportedly found a way to steal from smartphone users by exfiltrating the data read by their device's near-field communications (NFC) chip. If your debit card has an NFC chip on it (the "tap to pay"), it's possible. This presentation discusses two methods. One is skimming an NFC card and using the recovered data for making Card Not Present transactions online.
A new Android malware named NGate can steal money from payment cards by relaying to an attacker's device the data read by the near-field communication (NFC) chip. Specifically, NGate enables. ESET security researchers have discovered a new type of Android malware, which they call NGate. It can interact with a device’s NFC traffic, capture it from apps that use NFC, and relay the data to a malicious actor, who can then mimic or replay the intercepted data.
Cybersecurity researchers have uncovered new Android malware that can relay victims' contactless payment data from physical credit and debit cards to an attacker-controlled device with the goal of conducting fraudulent operations. Debit cards with NFC can be easily hacked to make fraudulent cash withdrawals and payments. But experts aren’t too worried about it in India. Here’s the reason for that.
nfc debit card scam
The cyberattack, based on both a complex social engineering scheme and the use of a new Android malware, is capable of stealing users’ near field communication data to withdraw cash from. The new chip-enabled credit cards that banks are sending their customers are supposed to make it more difficult for thieves to steal consumers' account information when they're using their.
nfc tag wifi connect
nfc debit card clone
cloning nfc card while in pocket
An NFC tag is a little sticker that contains some data. The Nexus 7, Galaxy SIII, and some other phones can read these tags to get the data. This is useful because you can place a sticker .
hacked with a micro sd card with nfc chip|nfc debit card clone