create rfid ghost tags Conclusion. RFID technology offers a powerful and versatile tool for tracking and managing assets. By understanding the core principles behind passive and active tags, communication protocols, manufacturing processes, and factors influencing read range and frequency, you can make informed decisions when deploying RFID solutions in your projects.
Yubico Authenticator for iOS is an authenticator app that adds a layer of security for mobile and desktop users. The Yubico Authenticator app for iOS allows users to interact with X.509 certificates stored in a YubiKey’s PIV .
0 · rfid tag setup
1 · rfid tag programming tutorial
2 · rfid tag programming tool
3 · rfid tag diagram
4 · rfid scanner
5 · how to make rfid tags
6 · arduino rfid tag diagram
Stats That Stood Out: Vikings-Saints. Jan 06, 2020 at 11:00 AM. Craig Peters. Senior Editor. The Vikings went the distance in overtime to defeat the Saints 26-20 in the Wild Card round on Sunday .

rfid tag setup
In this tutorial, we will provide a step-by-step guide to creating an RFID tag. We will start by discussing the necessary components and sharing a circuit diagram. Then, we will walk you through the process of gathering the . As an alternative to costly, heavy GPS tracking technology for monitoring . In this tutorial, we will provide a step-by-step guide to creating an RFID tag. We will start by discussing the necessary components and sharing a circuit diagram. Then, we will walk you through the process of gathering the materials, setting up the circuit, programming the Arduino, assembling the RFID tag, and finally, testing its functionality. As an alternative to costly, heavy GPS tracking technology for monitoring presence of small animals, Dr. Eli Bridge at the University of Oklahoma has developed a customizable Radio Frequency Identification (RFID) reader that you can build yourself on the cheap.
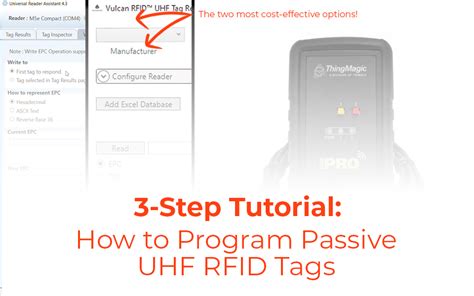
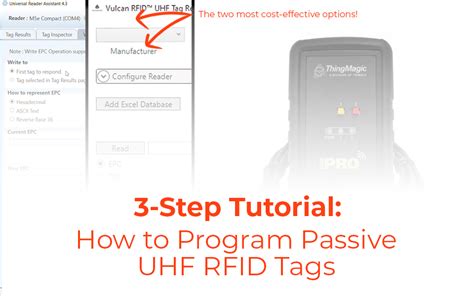
Once you understand the information above, you will need three things in order to program RFID tags - an RFID reader with an antenna, software to control the reader, and Passive UHF RFID tags. Today I’m going to walk through two options for a low cost and simple hardware and software solution. Conclusion. RFID technology offers a powerful and versatile tool for tracking and managing assets. By understanding the core principles behind passive and active tags, communication protocols, manufacturing processes, and factors influencing read range and frequency, you can make informed decisions when deploying RFID solutions in your projects. Learn how to program RFID tags and unlock the potential of this powerful technology in just a few simple steps. Boost efficiency and enhance security with our comprehensive guide.
Custom Tags. This is very unlikely to happen, mostly due to the RSA signature. Only Bambu has their "Private Key" which is used to digitally sign these tags. To create a custom key, you need to know the following info: UUID -> Encryption Key algorithm (or just use known UID + Key pairs) RSA Signature Private Key.Reading and writing data to and from RFID tags requires an RFID Reader and RFID Tags. With the help of the RFID Reader, the Raspberry Pi can read data from these RFID tags and at the same time write data into it. Keep reading below as I explain to you how to use RFID tags with simple Python scripts. The RFID system consists of two main components: an RFID tag and an RFID reader. The RFID tag has different formats. It can be a sticker like the one placed on supermarket products to prevent theft, on a plastic card, on a keychain, and . In this tutorial you will learn to use RFID tag with Arduino. SUPPORT OUR CHANNEL to grow, so that i can make more videos like these. Here are the ways by which you can contribute : 1.Whenever.
Serial Terminal Basics. This tutorial will show you how to communicate with your serial devices using a variety of terminal emulator applications. RFID Basics. Dive into the basics of Radio Frequency Identification (RFID) technology. SparkFun Qwiic RFID-IDXXLA Hookup Guide. In this tutorial, we will provide a step-by-step guide to creating an RFID tag. We will start by discussing the necessary components and sharing a circuit diagram. Then, we will walk you through the process of gathering the materials, setting up the circuit, programming the Arduino, assembling the RFID tag, and finally, testing its functionality. As an alternative to costly, heavy GPS tracking technology for monitoring presence of small animals, Dr. Eli Bridge at the University of Oklahoma has developed a customizable Radio Frequency Identification (RFID) reader that you can build yourself on the cheap.
Once you understand the information above, you will need three things in order to program RFID tags - an RFID reader with an antenna, software to control the reader, and Passive UHF RFID tags. Today I’m going to walk through two options for a low cost and simple hardware and software solution. Conclusion. RFID technology offers a powerful and versatile tool for tracking and managing assets. By understanding the core principles behind passive and active tags, communication protocols, manufacturing processes, and factors influencing read range and frequency, you can make informed decisions when deploying RFID solutions in your projects.
Learn how to program RFID tags and unlock the potential of this powerful technology in just a few simple steps. Boost efficiency and enhance security with our comprehensive guide.
Custom Tags. This is very unlikely to happen, mostly due to the RSA signature. Only Bambu has their "Private Key" which is used to digitally sign these tags. To create a custom key, you need to know the following info: UUID -> Encryption Key algorithm (or just use known UID + Key pairs) RSA Signature Private Key.
Reading and writing data to and from RFID tags requires an RFID Reader and RFID Tags. With the help of the RFID Reader, the Raspberry Pi can read data from these RFID tags and at the same time write data into it. Keep reading below as I explain to you how to use RFID tags with simple Python scripts.
The RFID system consists of two main components: an RFID tag and an RFID reader. The RFID tag has different formats. It can be a sticker like the one placed on supermarket products to prevent theft, on a plastic card, on a keychain, and . In this tutorial you will learn to use RFID tag with Arduino. SUPPORT OUR CHANNEL to grow, so that i can make more videos like these. Here are the ways by which you can contribute : 1.Whenever.
rfid tag programming tutorial
gemplus usb smart card reader mac
NFC – Contactless Cards: Brute Forcing Processing Options. Date: September 29, 2017 Author: Salvador Mendoza 3 Comments. In my previous post about NFC Contactless .
create rfid ghost tags|rfid tag setup