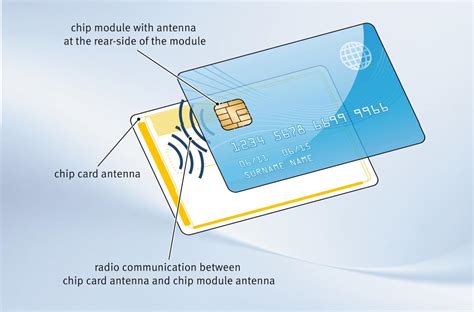
creating smart cards A smart card is a device that includes an embedded integrated circuit that can be either a secure microcontroller or equivalent intelligence with internal memory or a memory chip alone. The card connects to a reader with direct physical contact or with a .
ADF has won several religious freedom cases before the U.S. Supreme Court. "Freedom From Religion Foundation's twisted interpretation of the First Amendment has the .
0 · what constitutes a smart card
1 · smart cards used at banks
2 · smart card template
3 · smart card reader setup
4 · smart card creator
5 · how to create smart card
6 · example of smart card
7 · easy card maker
Simply hold the top area of your phone over an NFC tag, a notification will appear on the top of the screen. Press this notification and it will take you to the link. Native iPhone Scan. The iPhone must be running iOS11 .Posted on Nov 1, 2021 12:10 PM. On your iPhone, open the Shortcuts app. Tap .
There are several options for creating virtual smart cards, depending on the size of the deployment and budget of the organization. The lowest cost option is using tpmvscmgr.exe . By utilizing Trusted Platform Module (TPM) devices that provide the same cryptographic capabilities as physical smart cards, virtual smart cards accomplish the three key properties that are desired by smart cards: nonexportability, isolated cryptography, and .
There are several options for creating virtual smart cards, depending on the size of the deployment and budget of the organization. The lowest cost option is using tpmvscmgr.exe to create cards individually on users' computers. Alternatively, a virtual smart card management solution can be purchased to more easily accomplish virtual smart card .As a National eID card, smart health card, residence permit, or electronic passport, smart card technology offers more robust identification and authentication tools for both authorities' and citizens' benefits. You create virtual smart cards in the TPM, where the keys used for authentication are stored in cryptographically-secured hardware.A smart card is a device that includes an embedded integrated circuit that can be either a secure microcontroller or equivalent intelligence with internal memory or a memory chip alone. The card connects to a reader with direct physical contact or with a .
Virtual smart cards with Windows 10 are a great way to increase sign-in security without additional costs and extra hardware attached to end user PCs. If you have a TPM installed and your machine is encrypted, it simply involves creating the certificate template, creating the virtual smart card, and then issuing the VSC template to the end user.
The very basics. Public and private keys. Public key cryptography uses some very sophisticated mathematics to embed a secret inside a ‘private key’ from which a corresponding ‘public key’ is then generated. While related, it is generally “extremely difficult” to recreate the private key from the public key.Smart cards can be used for a wide range of programs, from keyless entry into a building or logging users onto computers and even paying for lunch in the cafeteria. But that flexibility can also make smart card technology hard to understand. This section will help you understand the differences between smart cards and their uses.
Smart cards are an extremely powerful and flexible technology to add to your card program – but if you don’t know how smart card technology works, how to order new smart cards, and whether you can print on the smart cards and use them as ID cards, it may seem overwhelming.
The working process of a smart card is comprised of the following steps: First, the smart card makes contact with the card reader, either directly or indirectly. The smart card reader receives the information stored on the chip. This information .
By utilizing Trusted Platform Module (TPM) devices that provide the same cryptographic capabilities as physical smart cards, virtual smart cards accomplish the three key properties that are desired by smart cards: nonexportability, isolated cryptography, and . There are several options for creating virtual smart cards, depending on the size of the deployment and budget of the organization. The lowest cost option is using tpmvscmgr.exe to create cards individually on users' computers. Alternatively, a virtual smart card management solution can be purchased to more easily accomplish virtual smart card .
As a National eID card, smart health card, residence permit, or electronic passport, smart card technology offers more robust identification and authentication tools for both authorities' and citizens' benefits. You create virtual smart cards in the TPM, where the keys used for authentication are stored in cryptographically-secured hardware.
A smart card is a device that includes an embedded integrated circuit that can be either a secure microcontroller or equivalent intelligence with internal memory or a memory chip alone. The card connects to a reader with direct physical contact or with a . Virtual smart cards with Windows 10 are a great way to increase sign-in security without additional costs and extra hardware attached to end user PCs. If you have a TPM installed and your machine is encrypted, it simply involves creating the certificate template, creating the virtual smart card, and then issuing the VSC template to the end user.
The very basics. Public and private keys. Public key cryptography uses some very sophisticated mathematics to embed a secret inside a ‘private key’ from which a corresponding ‘public key’ is then generated. While related, it is generally “extremely difficult” to recreate the private key from the public key.Smart cards can be used for a wide range of programs, from keyless entry into a building or logging users onto computers and even paying for lunch in the cafeteria. But that flexibility can also make smart card technology hard to understand. This section will help you understand the differences between smart cards and their uses.Smart cards are an extremely powerful and flexible technology to add to your card program – but if you don’t know how smart card technology works, how to order new smart cards, and whether you can print on the smart cards and use them as ID cards, it may seem overwhelming.
what constitutes a smart card
smart cards used at banks
There are a couple of NFC readers that will be able to read unencrypted cards. I personally use "NFC Tools". But sadly afaik there is no way to emulate on a nonjailbroken iPhone, since apple has locked the NFC emulation feature down to the Wallet app. This is so Apple can: Charge .
creating smart cards|what constitutes a smart card