what do virtual smart cards use for authentication This article describes the virtual smart card technology and how it can fit into your authentication design. Virtual smart card technology uses cryptographic keys that are stored on computers that have the Trusted Platform Module (TPM) installed. NFC can be used to read tags and for Apple Pay. To use, make sure your iPhone is unlocked, and then tap the top of your iPhone's back on the tag to get a pop-up. Unfortunately, .
0 · Virtual Smart Card Overview
1 · Understanding and Evaluating Virtual S
2 · Understanding Smart Card Authentication
3 · Provide strong Windows authentication
4 · Personal Identity Verification Card 101
5 · Get Started with Virtual Smart Cards
6 · Deploy Virtual Smart Cards
7 · About virtual smart cards
Python based reader/writer that is used to read tag data from the NFC ISO 14443 Type A and B cards, Mifare, FeliCa, and all 4 types of NFC (ISO/IEC 18092) tags. Code provides a basic framework used to grab tag data. #Environment Tested .libnfc-bin. libnfc is a library for Near Field Communication. It abstracts the low-level details of communicating with the devices away behind an easy-to-use high-level API. It supports most .
Virtual smart card technology offers comparable security benefits to physical smart cards by using two-factor authentication. Virtual smart cards emulate the functionality of .
Virtual smart cards are a technology from Microsoft that offers comparable security benefits in two-factor authentication to physical smart cards. They also offer more convenience for users and lower cost for organizations to deploy. Virtual smart card technology offers comparable security benefits to physical smart cards by using two-factor authentication. Virtual smart cards emulate the functionality of physical smart cards, but they use the Trusted Platform Module (TPM) chip that is available on devices. This article describes the virtual smart card technology and how it can fit into your authentication design. Virtual smart card technology uses cryptographic keys that are stored on computers that have the Trusted Platform Module (TPM) installed.
Virtual smart cards provide the benefits of physical smart cards without extra costs or hardware. They are based on a Trusted Platform Module (TPM) and authenticate users with a certificate against Active Directory, like a physical smart card.
For the purpose of authentication, one of the most common and effective uses of virtual smart cards is for Multi-Factor Authentication (MFA). Using multiple layers of security is key to maintaining network integrity, and a virtual smart card satisfies the “something you have” factor in authentication.A virtual smart card improves cybersecurity by adding an extra layer of authentication, ensuring that only authorized users can access sensitive information. It also protects against malware and viruses, as the virtual smart card cannot be physically stolen or damaged. How do you set up a virtual smart card? Smart cards are physical authentication devices, which improve on the concept of a password by requiring that users actually have their smart card device with them to access the system, in addition to knowing the PIN, which provides access to the smart card.
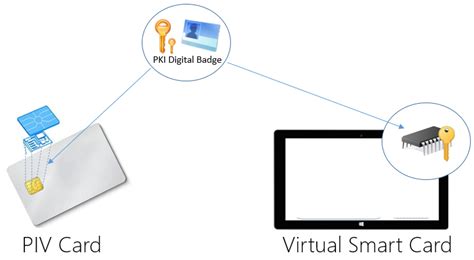
Virtual smart cards use PKI-based identities in a secure environment on laptops, to let users get rid of passwords and use strong authentication, signing and encryption in a smooth way. They work as physical smart cards, but without the need to issue and manage plastic cards or other hardware tokens. Customers using virtual smart cards are encouraged to move to Windows Hello for Business or FIDO2. For new Windows installations, we recommend Windows Hello for Business or FIDO2 security keys. Learn about the requirements for .
This document presents an overview of TPM virtual smart cards as an option for strong authentication. It provides a means for evaluating virtual smart card use in an enterprise deployment, in addition to providing information necessary for .
Virtual smart cards are a technology from Microsoft that offers comparable security benefits in two-factor authentication to physical smart cards. They also offer more convenience for users and lower cost for organizations to deploy. Virtual smart card technology offers comparable security benefits to physical smart cards by using two-factor authentication. Virtual smart cards emulate the functionality of physical smart cards, but they use the Trusted Platform Module (TPM) chip that is available on devices. This article describes the virtual smart card technology and how it can fit into your authentication design. Virtual smart card technology uses cryptographic keys that are stored on computers that have the Trusted Platform Module (TPM) installed. Virtual smart cards provide the benefits of physical smart cards without extra costs or hardware. They are based on a Trusted Platform Module (TPM) and authenticate users with a certificate against Active Directory, like a physical smart card.
For the purpose of authentication, one of the most common and effective uses of virtual smart cards is for Multi-Factor Authentication (MFA). Using multiple layers of security is key to maintaining network integrity, and a virtual smart card satisfies the “something you have” factor in authentication.
Virtual Smart Card Overview
A virtual smart card improves cybersecurity by adding an extra layer of authentication, ensuring that only authorized users can access sensitive information. It also protects against malware and viruses, as the virtual smart card cannot be physically stolen or damaged. How do you set up a virtual smart card?
Smart cards are physical authentication devices, which improve on the concept of a password by requiring that users actually have their smart card device with them to access the system, in addition to knowing the PIN, which provides access to the smart card.Virtual smart cards use PKI-based identities in a secure environment on laptops, to let users get rid of passwords and use strong authentication, signing and encryption in a smooth way. They work as physical smart cards, but without the need to issue and manage plastic cards or other hardware tokens. Customers using virtual smart cards are encouraged to move to Windows Hello for Business or FIDO2. For new Windows installations, we recommend Windows Hello for Business or FIDO2 security keys. Learn about the requirements for .
Understanding and Evaluating Virtual S
Step 3: How to Make Amiibo Bin File Backups with Tagmo. First, turn NFC on. Then, press “Scan Tag”. Finally, press the NTAG215 chip. “Scan“– if your phone’s NFC is turned on, hold an amiibo figure or card or NTAG chip and it will bring .
what do virtual smart cards use for authentication|Understanding and Evaluating Virtual S